Setting up Authentication via Reverse Proxy using Open iT Identity Server
Recommended reading: Open iT Identity Server
-
In the Open iT Identity Server installation directory, open
appsettings.json. This is by default inC:\Program Files\OpeniT\IdentityServer -
Check that the RedirectUris, PostLogoutRedirectUris, and BaseUri fields have correct values.
appsettings.json"IdentityServer": {
"Clients": [
{
"Enabled": true,
"ClientId": "00000000-0000-0000-0000-000000000000",
"ClientSecrets": [ { "Value": "****-REDACTED-****" } ],
"ClientName": "Caddy Authentication Client",
"AlwaysIncludeUserClaimsInIdToken": true,
"AllowAccessTokensViaBrowser": true,
"AllowOfflineAccess": true,
"AllowedGrantTypes": [ "authorization_code" ],
"AllowedScopes": [ "openid", "profile", "email", "roles", "offline_access" ],
"RedirectUris": [ "http://<core_server_uri>:<core_server_port>/auth/oauth2/generic/authorization-code-callback" ],
"PostLogoutRedirectUris": [ "http://<core_server_uri>:<core_server_port>/auth/logout" ],
"BaseUri": "http://<core_server_uri>:<core_server_port>",
"RequirePkce": false,
"AllowPlainTextPkce": false,
"Icon": "adminportal.svg"
}
]
},NOTEMake sure the
<ingress_hostname>and<port_number>are properly replaced. This is usually provided out of the box.For example:
appsettings.json"IdentityServer": {
"Clients": [
{
"Enabled": true,
"ClientId": "00000000-0000-0000-0000-000000000000",
"ClientSecrets": [ { "Value": "****-REDACTED-****" } ],
"ClientName": "Caddy Authentication Client",
"AlwaysIncludeUserClaimsInIdToken": true,
"AllowAccessTokensViaBrowser": true,
"AllowOfflineAccess": true,
"AllowedGrantTypes": [ "authorization_code" ],
"AllowedScopes": [ "openid", "profile", "email", "roles", "offline_access" ],
"RedirectUris": [ "http://WIN-HOST01:8080/auth/oauth2/generic/authorization-code-callback" ],
"PostLogoutRedirectUris": [ "http://WIN-HOST01:8080/auth/logout" ],
"BaseUri": "http://WIN-HOST01:8080",
"RequirePkce": false,
"AllowPlainTextPkce": false,
"Icon": "adminportal.svg"
}
]
}, -
Update the Authentications section properly, and remove the double slashes (//) at the beginning of the lines under Connections.
appsettings.json"Authentications": {
"LDAP": {
"IncludeLdapGroups": true,
"Connections": [
{
"FriendlyName": "MyLdap",
"Url": "192.0.2.xxx",
"Ssl": false,
"Port": 389,
"BindDn": "CN=<demo>,CN=<demo>,DC=<demo>,DC=<demo>,DC=<demo>",
"BindCredentials": "Password",
"SearchBase": "CN=Users,DC=<demo>,DC=<demo>,DC=<demo>",
"SearchFilter": "(&(objectClass=User)(objectClass=Person)(uid={0}))"
}
]
}
},Property Description FriendlyName Unique name of the LDAP connection Url Active Directory domain Ssl Status of the SSL (whether enabled or disabled). The default value is false. Port Port for LDAP. The default is 389. BindDn Contains the credentials to be bound inside the LDAP BindCredentials Password of the specified username in BindDn SearchBase Specifies where the search starts in the Active Directory structure for user account entries. Usually has the same value as the last four entries in BindDn. appsettings.jsonAuthentications
For example:
appsettings.json"Authentications": {
"LDAP": {
"IncludeLdapGroups": true,
"Connections": [
{
"FriendlyName": "Open iT LDAP",
"Url": "winhost01.example.test",
"Ssl": false,
"Port": 389,
"BindDn": "CN=john doe,CN=Users,DC=domain,DC=example,DC=local",
"BindCredentials": "Passwords",
"SearchBase": "CN=Users,DC=domain,DC=example,DC=local",
"SearchFilter": "(&(objectClass=User)(objectClass=Person)(uid={0}))"
}
]
}
}, -
Open the Task Manager, go to the Services tab, then restart the OpeniTIdentityServer service.
-
On a browser, go to
http(s)://<ingress_hostname>:<port_number>.<ingress_hostname>- hostname of the machine with Ingress installation<port_number>- port number used by the Apache web service; this is specified upon Ingress installation
-
On the login page, provide valid credentials, then click Login.
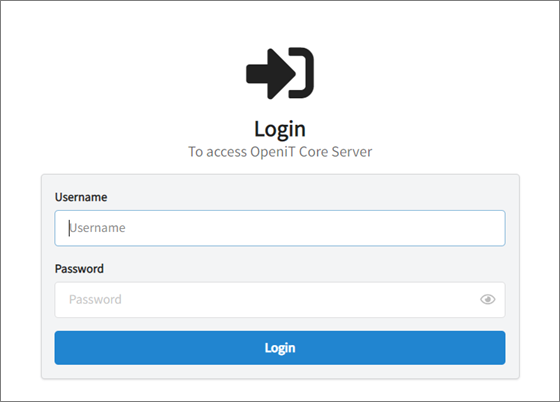 Login
LoginChange the password if you are logging in for the first time.
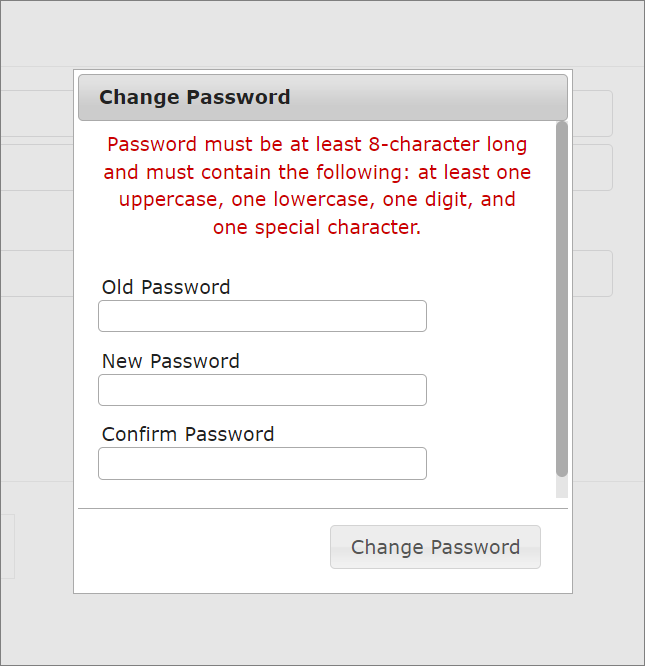 Change Password
Change Password -
On the Core Server web interface, go to Administration > Settings, then scroll down to the Authentication Settings.
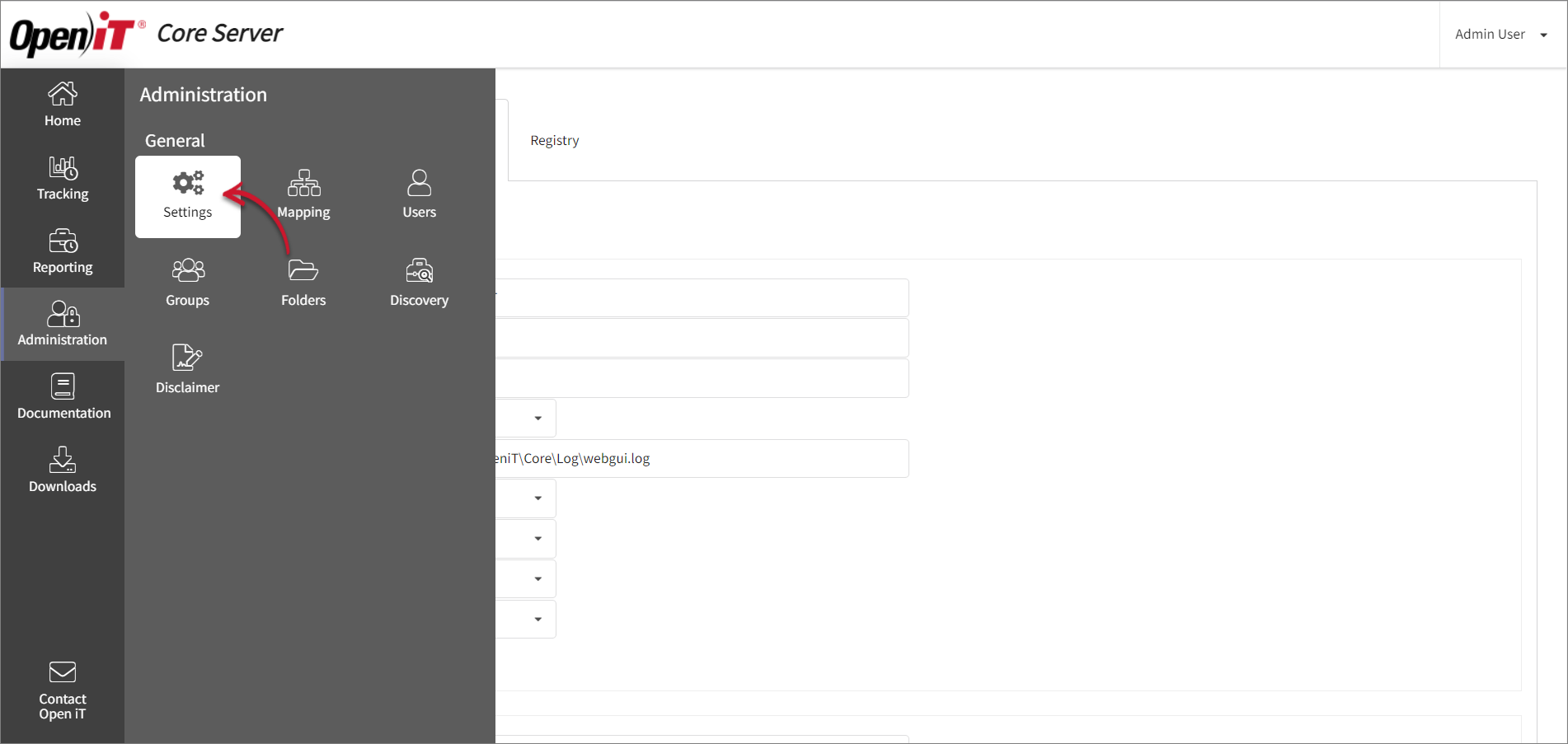 Administration Settings
Administration Settings -
Change the Authentication Type value to Authentication via Reverse Proxy, then click Save.
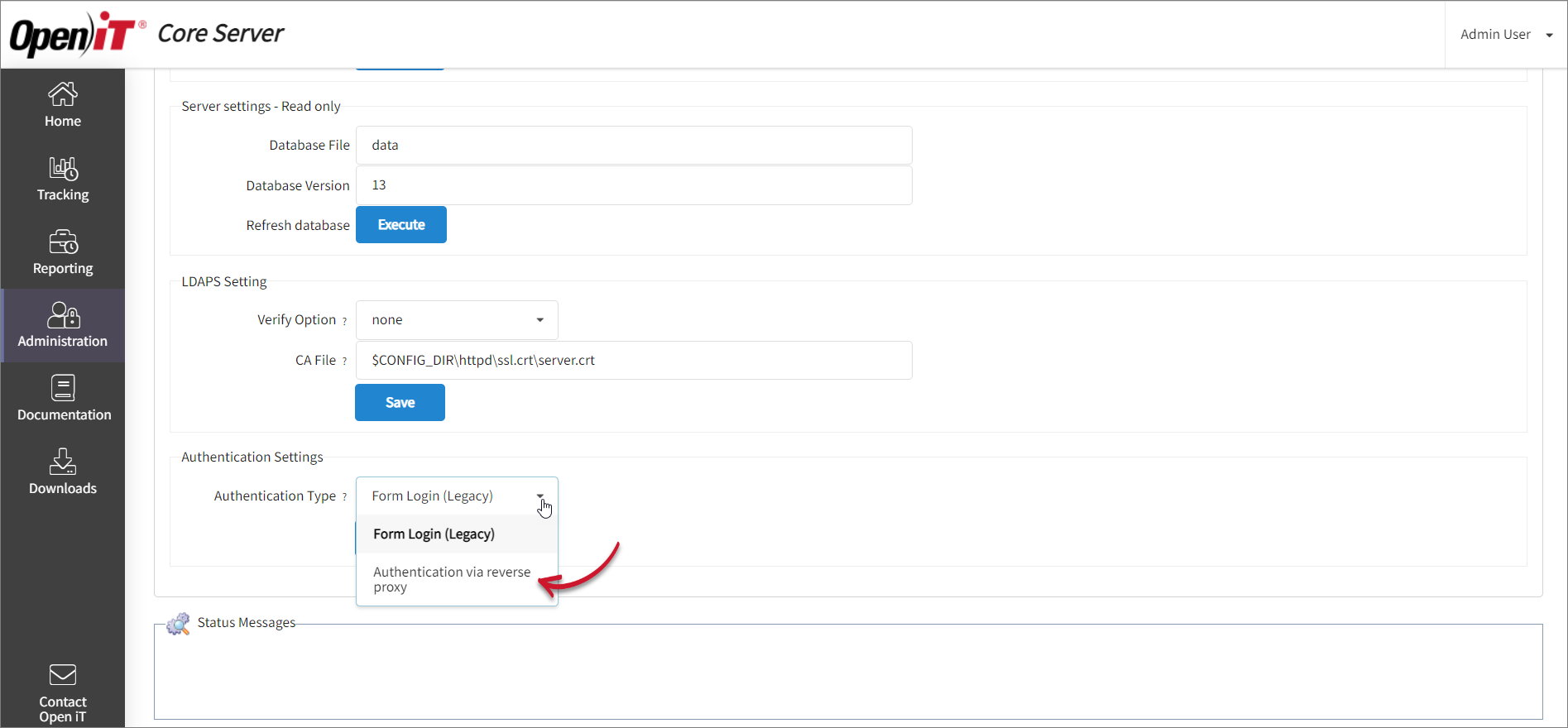 Change Authentication Type
Change Authentication TypeWait for the page to redirect to the login page while the Caddy server restarts.
 Change Authentication Manager
Change Authentication Manager